Windows Event Logs
Y'know, I can't help but get some Slumdog Millionaire vibes from this challenge. Like someone keeps asking me questions and I need to go back in the past to find out how I could answer that question from my own life experiences.
Hm.
Oh well, anyway!
Challenge Introduction
Grinchum successfully downloaded his keylogger and has gathered the admin credentials! We think he used PowerShell to find the Lembanh recipe and steal our secret ingredient. Luckily, we enabled PowerShell auditing and have exported the Windows PowerShell logs to a flat text file.
Please help me analyze this file and answer my questions. Ready to begin?
Question 1
What month/day/year did the attack take place? For example, 09/05/2021.
Answer: 12/24/2022
Question 2
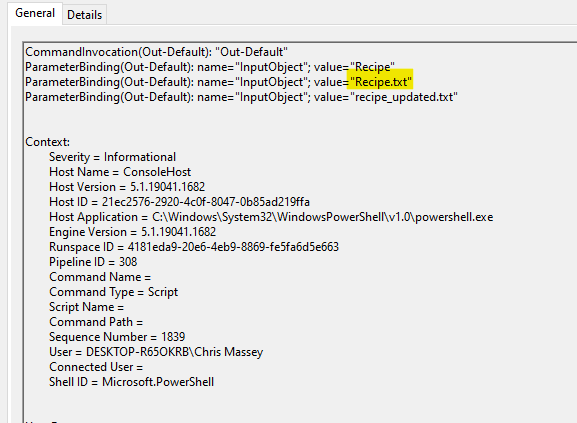
An attacker got a secret from a file. What was the original file's name?
Answer: Recipe.txt
Searched for Add-Content and found Recipe.txt and recipe_updated.txt.
Question 3
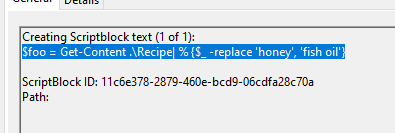
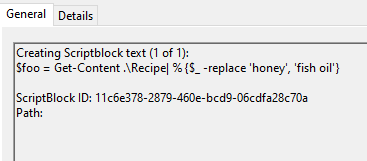
The contents of the previous file were retrieved, changed, and stored to a variable by the attacker. This was done multiple times. Submit the last full PowerShell line that performed only these actions.
Answer: $foo = Get-Content .\Recipe| % {$_ -replace 'honey', 'fish oil'}
Question 4
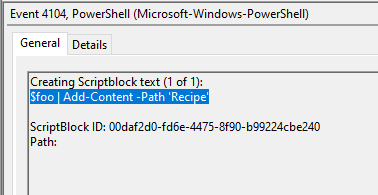
After storing the altered file contents into the variable, the attacker used the variable to run a separate command that wrote the modified data to a file. This was done multiple times. Submit the last full PowerShell line that performed only this action.
Didn't quite understand this, there were several accounts of similar commands. But this was what worked apparently.
Answer: $foo | Add-Content -Path 'Recipe'
Question 5
The attacker ran the previous command against a file multiple times. What is the name of this file?
Answer: Recipe.txt
Question 6
Were any files deleted? (Yes/No)
Answer: yes
Question 7
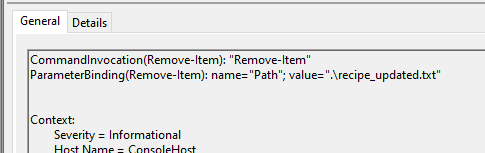
Was the original file (from question 2) deleted? (Yes/No)
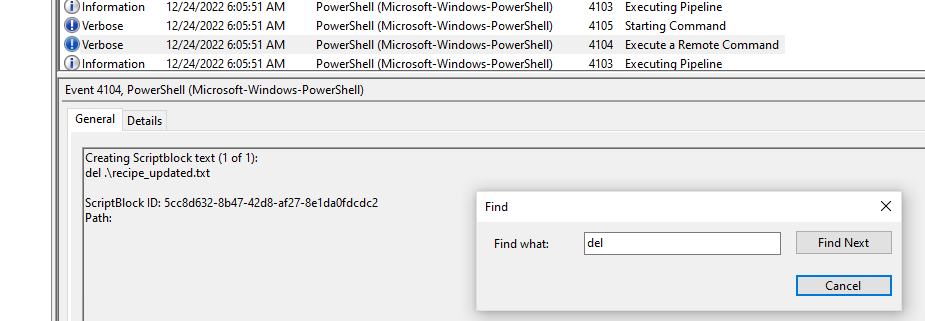
Answer: (no, see screenshot, recipe_updated.txt was deleted)
Question 8
What is the Event ID of the log that shows the actual command line used to delete the file?
Answer: 4104
Question 9
Is the secret ingredient compromised (Yes/No)?
Answer: yes
Question 10
What is the secret ingredient?
Answer: honey